Cyber risk: The silent killer in private equity

By John Martin CEO, Plutus Consulting,
Insight support by Matthew Jones, Rob Bachan and Somesh Mitra, Noremo UK
Private equity has mastered financial engineering, operational value creation, and buy‑and‑build, yet most firms are still underwriting deals as if cyber risk were an IT line item, not a balance sheet liability.
A single breach can now erase years of EBITDA gains and force abrupt multiple compression.
Recent data paints a sobering picture.
Cyberattacks on portfolio companies have surged, with ransomware up over 70% in two years and average breach costs now exceed $4.5M including fines, churn, and disruption.
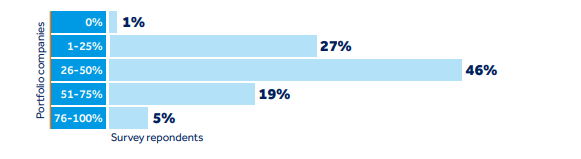
Over half of PE firms report cyber incidents in up to 25% of portfolio companies annually, 46% involving ransomware/extortion.
For private equity firms, the implications are profound and multifaceted.
The unpriced cyber debt on your balance sheet
Most mid-market assets carry hidden cyber debt legacy systems, unpatched infrastructure, no incident response, equivalent to 5-15% of enterprise value in unmodelled liabilities.
On day one, that technical debt becomes financial risk on your fund’s balance sheet – but it is rarely modelled, let alone priced.
Consider the reality: many middle-market companies acquired by PE firms operate with legacy systems, fragmented IT infrastructure, and minimal security protocols. These businesses often lack dedicated security personnel, rely on outdated software, and maintain inadequate incident response capabilities.
The moment a transaction closes, these vulnerabilities become the fund's liability, and the risk calcifies during the hold period.
As PE firms drive growth through acquisitions, geographic expansion, or digital transformation initiatives, the attack surface expands exponentially.
Somesh Mitra, Cyber Security Lead at Noremo comments, ‘in an acquisition, cybersecurity often slips into a “no man’s land”: the buyer assumes it’s handled, and the target assumes it’s not central to due diligence. That gap is exactly where attackers operate.’
Each new system integration, cloud migration, or third-party vendor relationship introduces additional entry points for cybercriminals.
Without a comprehensive security framework, portfolio companies become increasingly exposed precisely when they are undergoing their most significant transformations.
From IRR drag to outright deal breaker
The financial impact of cyber incidents on PE returns cannot be overstated.
A significant breach during the hold period can erase years of operational improvements and multiple expansion. Customer trust, once compromised, takes years to rebuild. Regulatory investigations can drag on for months, consuming management attention and legal resources that should be focused on value creation.
More troublingly, cybersecurity failures are increasingly becoming deal impediments.
According to Rob Bachan, Technology Director at Noremo, ‘the uncomfortable truth is that cyber exposure rarely comes from sophisticated zero-day attacks. It comes from what we assume is harmless: forgotten environments, legacy assets, and trusted partners. Winning organisations recognise that cyber resilience must be engineered before day one, embedded into diligence, and owned across the business, not delegated to IT once the deal is done.’
Sophisticated buyers now conduct thorough cyber due diligence during acquisitions. A portfolio company with weak security posture, a history of incidents, or unresolved vulnerabilities will face valuation haircuts or, in extreme cases, deal termination.
PE firms that neglect cyber readiness throughout the hold period may find their exit strategies fundamentally compromised.
The regulatory environment compounds this pressure. With frameworks like GDPR, CCPA, and emerging SEC cybersecurity disclosure rules, the compliance burden has intensified. Portfolio companies that fail to meet these standards face not only fines but also restrictions on data processing that can hamstring business operations in key markets.
Make cyber a value‑creation lever, not a compliance chore
Forward-thinking PE firms are reconceptualising cybersecurity not as a technical IT issue but as a critical component of enterprise value. This shift requires embedding security considerations throughout the investment lifecycle.
During due diligence, this means conducting comprehensive cybersecurity assessments that go beyond compliance checklists. Firms should evaluate the target's security architecture, incident response capabilities, vendor risk management, and data governance frameworks. Understanding the true cyber risk profile allows for more accurate valuation and informs the post-acquisition integration strategy.
In the first 100 days, cyber should sit alongside pricing, sales effectiveness and working capital on the value‑creation agenda. At a minimum, which means:
- Portfolio-wide inventory of critical assets and crown-jewel data.
- Enforced basic cyber hygiene across the estate.
- Assessed, board-approved incident response plan, before the breach hits.
Throughout the hold period, regular security assessments, tabletop exercises, and board-level cyber risk reporting should become standard practice. Portfolio companies should develop and test incident response plans, ensure business continuity capabilities, and maintain updated asset inventories. These measures not only reduce risk but also demonstrate to potential buyers that the company takes security seriously.
Cyber maturity as a valuation premium
PE firms that embed cybersecurity into their operational value creation strategies gain multiple advantages. Portfolio companies with mature security postures face fewer disruptions, maintain stronger customer relationships, and avoid the productivity drain of responding to incidents. They are better positioned to pursue digital transformation initiatives because security considerations are built into these projects from inception rather than bolted on as afterthoughts.
During exit processes, demonstrable cyber maturity becomes a competitive differentiator. Buyers increasingly view strong security practices as indicators of operational excellence and management sophistication. Portfolio companies that can present comprehensive security documentation, clean audit histories, and well-tested response capabilities command premium valuations and experience smoother transaction processes.
Most importantly, proactive security investment protects the fund's reputation. In an environment where LPs scrutinise ESG factors and operational practices, a single catastrophic cyber incident at a portfolio company can damage relationships with institutional investors and complicate future fundraising efforts.
A call to action for PE leadership
The question facing private equity firms is no longer whether to invest in cybersecurity but how to integrate it effectively into their value creation frameworks.
This requires several concrete steps.
First, PE firms should develop cyber due diligence capabilities, either through internal expertise or trusted advisory partners who understand both security and the operational realities of middle-market businesses.
Second, firms should establish clear security expectations for portfolio companies, with board-level oversight and regular reporting on key risk indicators.
Third, PE firms should facilitate knowledge sharing across their portfolios, allowing portfolio companies to learn from each other's experiences and leverage collective buying power for security tools and services.
Finally, PE firms should view cybersecurity spending not as a cost centre but as an investment in enterprise value protection and enhancement. The marginal cost of implementing robust security controls pales in comparison to the potential value destruction from a significant breach.
Conclusion
The cybercrime landscape will only grow more sophisticated and aggressive. Threat actors hunt PE assets for their data richness and security gaps.
Firms institutionalising cyber now will safeguard IRR, smooth exits, and win LP scrutiny.
Plutus hard wires this into DD through value creation; Noremo quantifies the risks at scale. Start with our "cyber QoE" assessment for any asset or portfolio.
For PE leadership, the question is no longer ‘should we invest in cyber?’ but ‘how quickly can we integrate it into every stage of the deal lifecycle?’
Over the next 12–24 months, the firms that institutionalise this will protect IRR, reduce exit friction, and differentiate with LPs who increasingly scrutinise operational resilience.
The firms that will thrive in the next decade are those that recognise cybersecurity not as a technical obligation but as a fundamental component of operational excellence and enterprise value.
The time to act is now.
Plutus Consulting partners with GPs to hard wire cyber into commercial and technical due diligence, 100‑day planning and value creation blueprints, while Noremo brings the diagnostic tooling and threat‑intelligence needed to quantify and track cyber risk at portfolio scale.
To see what your current exposure looks like, and where value is at risk, we start with a rapid “cyber quality of earnings” style assessment across a single asset or your whole portfolio.





Member discussion